For years, numerical passcodes and alphanumeric passwords were how we kept trying eyes away from the contents of our devices. Now, smartphone manufacturers have stepped things up a notch by complementing the regular form of smartphone security with biometric authentication. And quite impressive enough, smartphones now sport biometric authentication tools that are were only possible on high-end computers. We highlight all the biometric authentication technology that have been successfully implemented on mobile phones over the years, their advantages, downsides, prospects they hold, and smartphones that support each authentication methods.
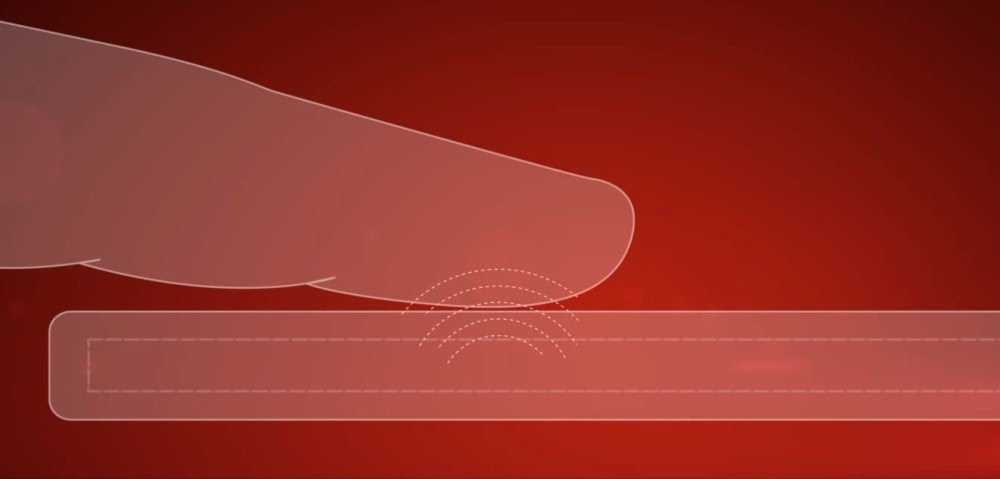
Fingerprint
The fingerprint sensor or reader is one of the earliest biometric authentication technology to feature on a smartphone. The history of fingerprint authentication on smartphones dates back to 2004 when a South Korean company announced the Pantech GI100. The device was the first ever device to have a fingerprint scanner for authentication and speed dialing purposes. However, some sources opine that Apple started the modern-day fingerprint scanner revolution when it launched the TouchID with the iPhone 5s. There are basically three types of fingerprint scanners used on smartphones and they differ in how they function and scan prints. Optical scanners / sensors These are the oldest types of sensors used on smartphones. These sensors use a light source to capture a high-resolution photograph of your finger (read: prints) and uses algorithm to identify unique patterns. Capacitive sensors Unlike optical sensors that takes an image of your finger, capacitive sensors make use of capacitor circuits (its core component) to collect fingerprint data. This type of sensor is most used fingerprint sensor. Ultrasonic sensors
This is a new sensor that was introduced by Qualcomm in 2016 on the LeeCo Le Max Pro. This sensor uses a transmitter to send ultrasonic pulse against your finger to create 3D details of your prints. Only ultrasonic sensors reproduce and store prints in 3D, making the ultrasonic system more secure than 2D versions created by optical and capacitive sensors. Pros of Fingerprint scanning Fast unlock time Can be used for other purposes (like payment authentication) aside device unlock Cons of Fingerprint scanning Smartphone can be unlocked without user’s consent i.e when sleeping
Iris Scanner
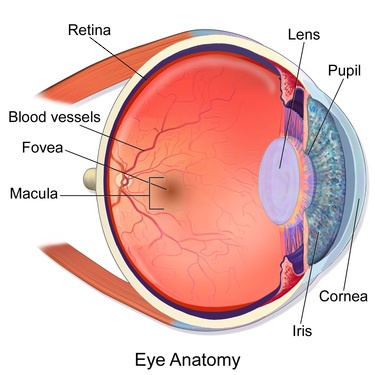
Iris scanning isn’t a very much popular biometric authentication method on a smartphone, it is also more sophisticated way of securing your smartphone. And though Iris scanning is commonly and mostly used on Samsung Galaxy flagships, the technology was first used on a phone — Fujitsu ARROWS NX F-04G — by Japanese company Fujitsu. How does Iris Scanning work? The Iris is a thin and circular structure in the eye. It adjusts the size of the pupil and also responsible for controlling the amount of light that enters the eye. Interestingly, just like fingerprints, no two humans in the world have exactly the same Iris. The Iris scanner of your smartphone flashes near-infrared (NIR) light into one or both of your eyes to recognise your iris(es) and unlocks your device. The NIR light emitted by the iris sensor is safe and poses no risk to the user. Pros of Iris Scanning
Iris Scanning is more accurate — unlike fingerprint (40), the human Iris has 225 different points of comparison. Secures your device while you’re asleep.
Cons of Iris Scanning
Iris scanners are expensive. Thus making phones with iris scanning capabilities generally pricier. Iris scanners can be fooled by a high quality (face or iris) image. Iris capture can be delayed if a user isn’t looking properly into the camera or if head isn’t still. Scanning under direct sunlight can be a problem since the iris may be obscured by bright reflections.
Some smartphones with Iris Scanning method of biometric authentication include Samsung Galaxy S9 Plus, Samsung Galaxy Note 9, LG G6, HTC U11 etc
Voice Recognition
Also known as Voice ID, Speaker recognition, or Voice Biometrics, Voice recognition is an authentication method that grants access to a device by identifying a user’s unique voice pattern. When identifying and differentiating between voices, a device’s voice recognition software takes the following unique voice biometrics into consideration: sound, rhythm, pattern, dialect, speaking style, pitch, format frequencies and spectral magnitudes. Pros and Cons of Iris Scanning Voice recognition is also quicker, easier, and relatively more secure. However, there are reports and fears that a good mimic can bypass voice recognition authentication.
Facial Recognition
Although Facial Recognition only recently became popular when Apple introduced to the iPhone X as Face ID, the isn’t the first instance the technology would be used on a smartphone. Facial Recognition as a form of smartphone security dates back to 2005 when ORMON Corporation, a global leader in automation, control technology, and sensing announced the OKAO Vision Face Recognition Sensor (which could be used on mobile phones, PDAs, and a y camera-enabled device) in Japan. How does Facial Recognition works? Depending on some factors like the manufacturer of your smartphone, facial recognition are of different types, have varying characteristics as well as patterns of functioning. Majorly, many smartphones that comes with the feature usually use the front-facing camera and dedicated software to record an image and properties of your face. Presently, there are many smartphones that comes with Facial recognition capabilities but Apple’s Face ID (on the iPhone X and subsequent iPhones), despite its shortcomings, is one of the most sophisticated. Face ID uses an IR beam projector and Infrared camera to create a 3D model of your face; it measures distance traveled by each beam before they hit your face. It is also the most effective, precise, accurate and safest facial recognition system ever used on a smartphone. Unlike most other facial recognition systems, Face ID takes extrinsic properties of the face like facial hairs, accessories into account. Its effectiveness isn’t hindered by growth or accessories as Face ID software automatically and occasionally recaptures and updates your facial template. Pros
Convenience — Facial Recognition might not be the safest method of biometric security, but you don’t have to tap buttons, keys, or touch any part of your smartphone before it unlocks. Fast and easy to set up Effectiveness not hindered by facial growth and accessories
Cons
Intruders can gain access to your device if you’re asleep by simply placing your phone to your face.
Generally and conclusively, biometric authentication can not entirely replace PIN, passwords, patterns, code etc in terms of security and reliability, they can only supplement. Some of these biometric security systems are still in their early stages and undergoing research and development. Fingerprint sensors, for example, are now being placed under displays. Facial recognition are also becoming faster. It is becoming pretty much obvious that biometric means of authentication is the future of smartphone security.