The internet is a beautiful place; a medium to obtain & exchange information, work, have fun, make money, communicate, meet people, learn stuff, and do a whole lot more. However, despite the good that the internet has to offer, things can get really ugly as well. In so many different ways, people have been scammed on the internet, their monies (and identities) have been stolen, accounts have been compromised and so on. And these things are avoidable. Carefully go through this guide to have a full understanding of how you can stay protected on the internet — on mobile & mobile apps, PC & desktop software, etc.
A. General Security and Authentication
i. Protect yourself from other individuals
Before now, a good number of internet users accessed the web via laptops and desktops. Things are quite different now as smartphones and mobile apps have disrupted PC. And since, unlike PC, smartphones can get stolen or misplaced easily, the very first step of securing your online accounts is creating strong passwords, PINs, and patterns. Biometric authentication methods like fingerprint, Face ID, Iris scanning, and Palm Unlock are also other secure ways of protecting your smartphone and mobile app. There are times when you aren’t sure if your account passwords have been compromised or not. There are certain tools (like Google Chrome’s Password Leak Detection) that help you figure out which of your passwords have been compromised in data breaches. The list below contains links to useful information, tutorials, and guides that’ll help you strengthen your mobile and app security. And ultimately, protect you from any harm on the internet. Useful Links:
Complete Guide to Smartphone Biometric Authentication: (Fingerprint, Iris, Voice, Face ID)Why you shouldn’t use Fingerprint/Touch ID and Face IDHow to enable Password Leak Detection in ChromeGoogle Chrome’s new extension checks if your Password has been breachedHow to change or reset forgotten Google passwordHow to change or reset forgotten Facebook passwordHow to password protect your Android AppsHow to recover a hacked Facebook account
ii. Creating Strong Passwords
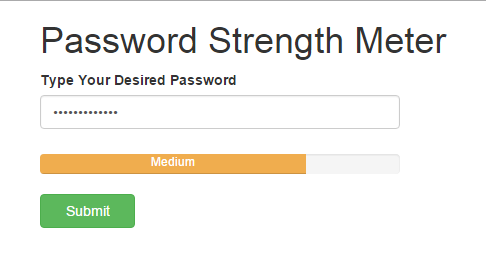
Anything worth doing is worth doing well, they say. The same applies to creating passwords to safeguard your accounts on the internet. You shouldn’t just create passwords for the sake of it. Your password should be “strong”. It should contain a balanced mix of certain elements and ultimately, be very difficult to hack, guessed, or bypass. And yes, there are some passwords you should NEVER use to secure your accounts. Check them out. If you’re having a hard time creating a strong password, you should check out our detailed guide on creating strong passwords. Alternatively, you can use password managers — software/apps that suggest strong passwords for your online accounts and also helps manage all your passwords so you don’t have to always remember them. Useful Links
What makes a password “strong”?How to use the Google Password Checkup extension to keep your accounts secureThese are the Top 25 Worst passwords of 2018How to Use a Firefox Master Password to Protect Stored Logins and Passwords
iii. Two-Factor Authentication — Passwords aren’t enough
Sometimes, it’s not even enough having a strong password; you should further beef up your mobile account’s security via 2-Factor Authentication (also called 2FA or 2-Step Verification). Enabling 2FA in your online accounts will require you input some sort of code (in addition to your password) which would be sent to your phone number as a text, to a physical token, or the authenticator app on your smartphone. We have put together a comprehensive guide on everything you need to know about 2-Factor Authentication — when, why and how to use it to secure your account online. Other Useful Links
Lock down your Google and Facebook account with Two-Factor Authentication (2FA)Correctly Configure Two-Factor Authentication before you’re locked out of your own accountHow to sign in to a 2FA-enabled Google account when you lose your phoneHow to Increase your Online Security by Enabling Two-Step Verification
B. Online & Web Privacy
Because the internet is filled with hackers, spammers, sniffers and prying eyes with evil intents waiting to steal your data at every chance they get. This is why it is important to keep yourself (and your information) protected at all times.
i. VPN & Proxies
As earlier mentioned, the internet is one place where you want your privacy respected on all fronts. However, this is something you need to pay keen attention to because the hackers are also not sleeping. One way to keep your online privacy strong is by concealing your internet traffic. And you can achieve that using VPN and Proxies. Asides from bypassing geo-restrictions, VPNs and Proxies are also brilliant ways to conceal your identity from evil eyes on the internet. You can learn more about using VPNs and Proxies to safeguard your activities on the internet via the links below. Useful Links
What Exactly is a VPN (Virtual Private Network) and Why You Still Need OneThe difference between a Proxy and a VPNHow to Keep Your Internet Traffic Private from AnyoneHere’s how to choose between Free and Paid VPNHow to selectively use VPN for specific Apps only on your phoneCloudflare’s WARP is a Free fast VPN with no Ads. Here’s how to get it
ii. DNS-over-HTTPS
Hackers, spoofers, and individuals aren’t the only ones that constantly lurk on the internet to steal your data. Corporations do it too. Sometimes, your internet service provider (ISP) harvests personal data about your activities on the web and sells to third-parties —who in turn use such info for advertising targeting— without your consent. Not all ISPs do this but the truth is, there’s really no way for you to find out if they do… or not. What you can do, however, is to use privacy-focused technologies like DNS-over-HTTPs to protect your personal privacy on the web. You can further read about such technologies and how to use them to safeguard yourself and your data on the web. Useful Links
What’s DNS-over-HTTPS (DoH) and DNS-over-TLS (DoT) and why it’s controversialHow to Enable DNS-over-HTTPS(DoH) in Firefox and Chrome browsersHow to change DNS server on Windows, Mac and LinuxHow to change the DNS Server on your Phone
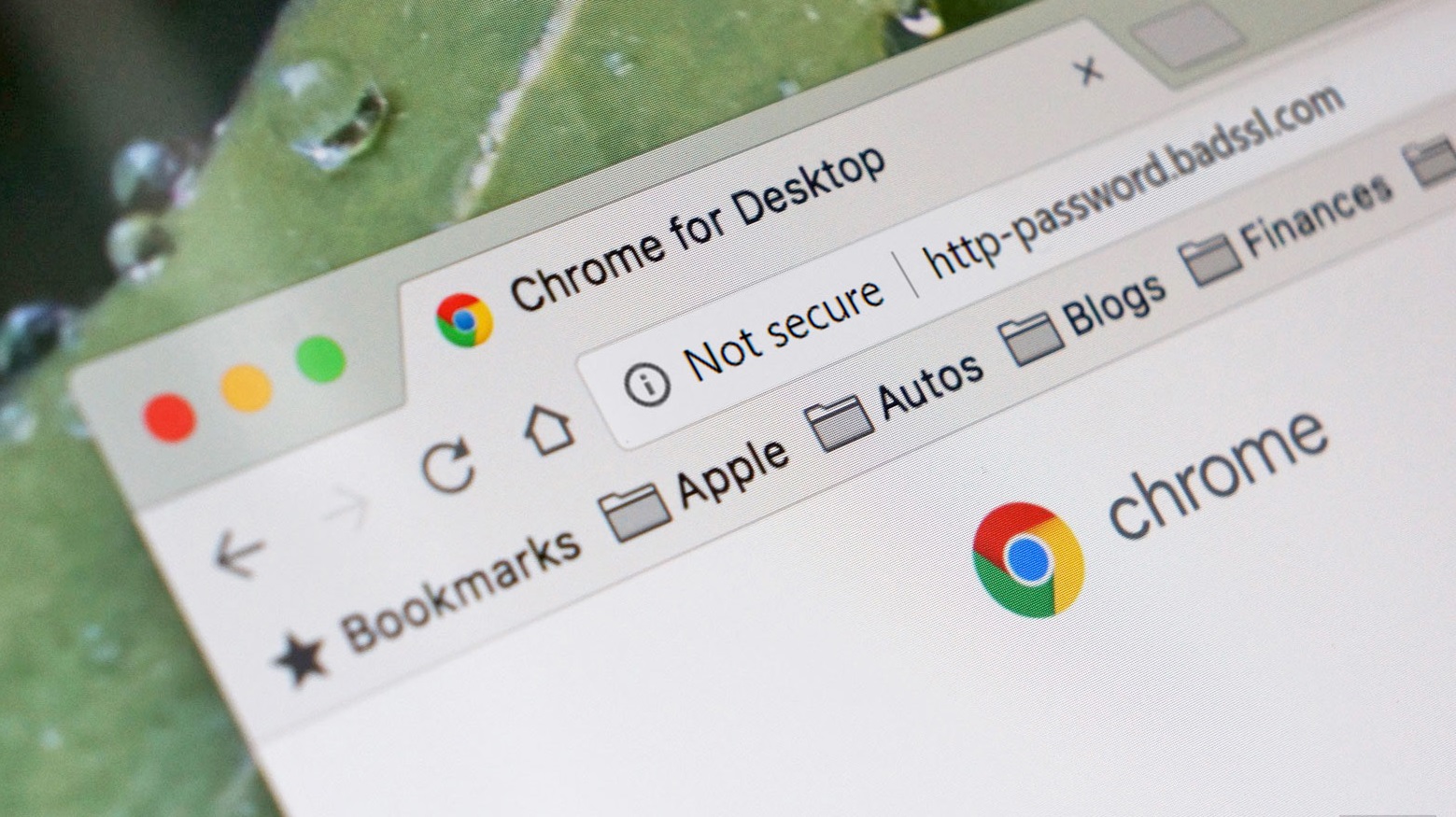
iii. HTTPS & SSL certificates
When you surf the web in your browser, some websites URL start with http:// and some, https://. The additional “S” has a meaning to it and you should ensure that whatever website you’re surfing on the world wide web has a https:// at the beginning of the URL. The extra S stands for Secure Sockets Layer (SSL) and is an indication that your connection with the website is private and whatever information you provide on the site cannot be intercepted by a third-party who may want to use it for fraudulent activities. Whenever you’re surfing a website that doesn’t have the SSL certificate, some browsers (especially Chrome) will alert you that the website isn’t secure. Whenever you this warning, make sure you do not provide sensitive information on the website. HTTPS and SSL certificates generally slap an extra layer of security to your online activities. can learn more about HTTPS and SSL certificates in the links below. Useful Links
What are SSL certificates? Understanding how useful they areWhy do website addresses start with http:// or https://Should be worried about “not secure” chrome warning on non-https websites?For website owners — A complete guide to running your website securely on https
iv. Privacy-focused Browsers & Search Engines
Not sure if you know this but the moment you log onto the internet, you leave a trace that tells a lot about you to certain people and corporations. Your browser, for example, knows more than you think. Asides the fact that it (your browser) takes note of your browsing history, other data like location information, operating system details, plugins installed, time zone the computer is set to, language, screen size and other information are garnered through a process known as “fingerprinting”. Some browsers are also not generally secure and allow hackers and third-parties access your data so easily. That’s why should consider using privacy-focused browsers. These privacy-focused web browsers limit ads, incessant spam, monitoring, and tracking to the barest minimum. About search engines, they also collect and harvest a lot of your personal information. That’s the (hidden) price you pay for using their services for free. The solution to keeping your private information private when searching for information online is to use privacy-focused search engines — DuckDuckGo is a good example. Useful Links
Getting started with DuckDuckGo, the privacy-focused search engineTop 5 Privacy-focused Browsers To Have on Your DesktopHere’s what your Browser knows about you
v. Disposable Email Providers
Another service that you can use to beef up your online privacy & security is Disposable emails. Also known as “Throw-away email”, “Tempmail”, “Fake-mail”, or “Trash mail”, Disposal email providers offer these service that allows you receive emails at a temporary address that self-destructs after a certain time elapses. No sign-up or password is required. Disposable email also helps you avoid malicious spam messages that pile up in your inbox. Another use case of disposable emails is when some retailers, websites, and blogs ask you to register before you view certain content, post comments or download something but eventually end up spamming your inbox. Useful Links
Top 3 disposable email addresses service providers
vi. Phishing and Scams
For noobs and newbies, phishing is when hackers or evil perpetrators maliciously keep (and operate) a false website or send a false e-mail with the intent of masquerading as a trustworthy entity with the intent of acquiring sensitive information such as usernames, passwords, login credentials, credit card details, etc. Learn more about some common online phishing and scam techniques and tricks and how to protect yourself. Useful Links
How to avoid Phishing Online5 ways to protect yourself from Ransomware
C. Mobile Security
Because the majority of the online activities (shopping, social media, gaming, surfing, movies, streaming, etc) happen on our smartphones and tablets through mobile apps, it is important to learn how to keep your privacy intact while using them.
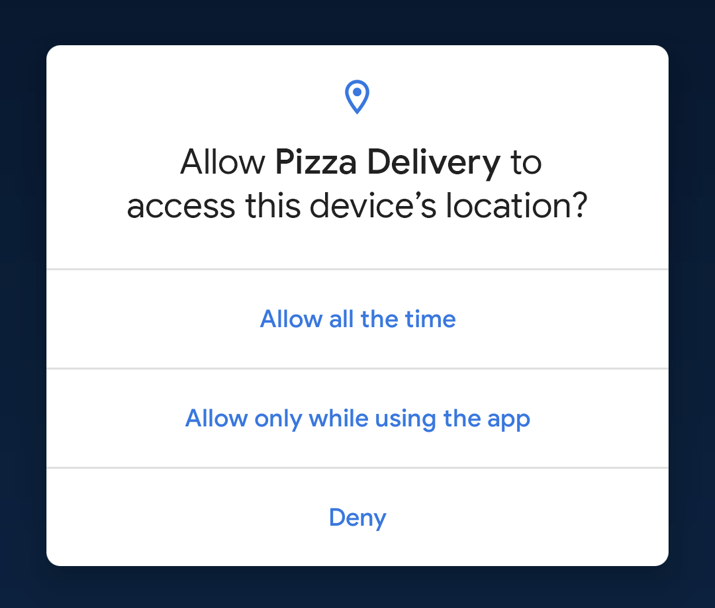
i. App permissions
When you newly install an app, it mostly requires you to approve certain permissions. These permissions usually give these apps access to personal & private information like your location, files, microphone & mic recordings, and other data that can be used to track you. The links below will navigate you through things you need to do to keep your private info from the reach of certain apps. Useful Links
Android Permissions: What do apps have access to on your device?App permissions you should keep an eye onWhat to consider before installing an app on your phoneHow Geo-tagged photos give away your locationHow to Prevent Facebook from Background Location Tracking on Android
ii. Pop-up Ads
Pop-ups and malware are another thing you should keep an eye out for. These are malicious apps designed to steal your information and also cause damage to your device. Pop-ups drain your phone’s battery, increase your device temperature, and generally make your device run slower. Worst part is that they are “stubborn” i.e. sometimes very difficult to uninstall or remove fro your device. Read more
How to Stop and Remove Pop-up Ads on Android devicesIf you have any of these 85 apps on your Android smartphone, UNINSTALL them now
iii. Geo-tagging
Despite the fact that the average internet user is now more privacy-conscious about the type of information shared online, we still subconsciously give out certain (sensitive) data without even realizing it. Geo-tagging is the process of attaching location information to media files like photos and videos. When a media file is “geo-tagged”, it basically means that the device (digital camera, smartphone, tablet, etc.) that captured the file has embedded GPS coordinates in the file metadata. Although geo-tagging a photo has some useful applications like helping you organize pictures in your gallery based on location, it also comes with its associated (privacy) risks too. A stranger can download your pictures on the internet, extract GPS coordinates and track you. Read more to learn how to remove location data from photos you take on your smartphone. Useful Links
How Geo-tagged photos give away your locationShould you always have your phone’s GPS Location turned on?
D. Banking, Payments & Mobile Money
The rise of eCommerce, cryptocurrency, mobile money, fintech apps, payment apps, virtual cards and the like have subsequently increased how much people transact over the internet. In Africa and across the globe. Equally, the number of time people have been scammed while transacting online and their assets stolen have likewise increased. Since the majority of transactions carried out online are performed using credit and debit card, it is important to know the anatomy of your banking (debit and credit) cards, measures you can take to avoid being defrauded, as well as what you should do if your card/logins are stolen. As an added layer of security when transacting online, ensure that extra authentication steps like 2-Factor Authentication and One-Time Password/PIN (OTP) are enabled on your banking and payment apps. The articles linked below contain everything you need to know about staying safe while transacting online. Useful Links
Debit and Credit card number, CVV and Expiry date explainedDebit card vs. Credit card: What are the differences?How to avoid credit/debit card fraudWhat you can do when your Debit/ATM card is stolenWhat is one-time password or one-time PIN (OTP)?How to change your Mobile Money PIN. (MTN, Airtel and Africell)What happens if someone steals your mobile money PIN?How to change your Safaricom M-PESA PIN
E. Email Protection
Email is one of the most used media of communication, both for personal and business purposes. There are about 4 billion email users worldwide and over 293 billion emails are sent each day (according to 99firms.com). As such, email (and email accounts) are mostly targetted by hackers and spammers. There are a lot of security methods listed above that helps protect your emails but we’d be linking more email security resources and tips below. Emails are secure, but not always. If you had previously granted any third-party apps, software or developers access into your inbox, they can read your emails. So you should review the permissions you might have given to third-party apps in the past. You might also want to confirm that your email provider offers end-to-end encryption. Useful Links
5 email providers that offer end-to-end encryptionHow to Block third-parties from accessing your GmailHow to reset your Yahoo password
F. Social Media
Everyone uses social media but not everyone is using it safely. By safely, we mean what are the things your social media platforms know about you? Do they collect more data than you permit them to? What type of information does your social media platforms collect from your (and behind your back)? Are your social media accounts well-protected from hackers? So many questions. Luckily, there are answers to all of them. In this era where many social media platforms have been caught harvesting and selling their user data to the highest bidder, using social media safely and being conscious of what data they obtain from you is quite important. The links provided below might help you. Useful Links
10 ways you can improve security of your Facebook accountHow to delete auto-uploaded phone contacts on MessengerSocial Media, Election fever and how to protect yourself online from your governmentHow to view & download all your WhatsApp account informationHow to download your Twitter account informationHow to delete your phone contacts uploaded on FacebookHow to delete your Facebook Account PermanentlyHow to recover a hacked Facebook account
Wrap up
Just as technology keeps evolving, privacy (and security at large) as an aspect of the internet will also keep on evolving. Currently, the links and materials listed above will solve a good number of privacy and security challenges that you (as a user/consumer) currently face. As more privacy-focused technologies and solutions are developed, we’ll add them to this list as soon as possible. So ensure you bookmark this page on your browser if you really do care about privacy.